One way to search event logs across not one but hundreds of servers at once is with PowerShell. The Windows event log is a record of all events – information, warnings and errors – produced by a Windows computer. The N-central Windows Event Log Monitoring service enables you to monitor this centralized log and filter out those considered important to generate notifications. Lansweeper provides IT professionals with a highly accurate event log viewer feature. Lansweeper functions as an all-in-one solution that does more than a regular event log scanner.
Refactoring previews for Code Actions are also accessible from the new Code Action control. Custom keybindings are supported for selection of Code Actions, as well as to preview the selection. The new setting terminal.integrated.shellIntegration.decorationsEnabled lets you display command decorations in either the gutter, the overviewRuler, or neither.
Get Proactive About Tracking Application Errors!
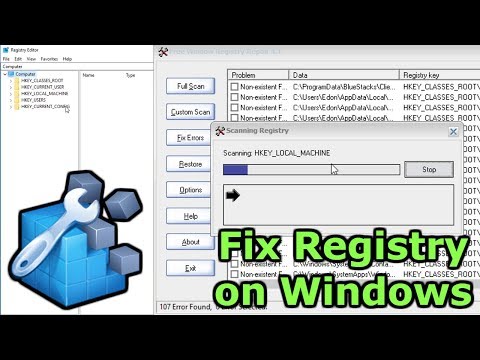
The process often takes a few minutes after which the PC will restart in order to save the changes. That’s all you need to do to have the system’s registry restored here on your PC. It is the fastest and the most reliable registry cleaner program. It is recommended to clean your Windows registry periodically.
- If I start to get more of these calls, I may have to start trying to take up more of their time, just for grins .
- This will reduce the chances of the drive becoming corrupted or damaged.
- Experimental support for the M1 architecture was added in node.js v15.3 and full support was added in v16.0.
Then, type in each of the subsequent instructions one at a time and hit Enter to carry them out. Complete the driver rollback procedure by following the on-screen prompts. After restarting, check whether the Netwtw04.sys problem still exists. In order to access the Run dialogue, press the Win key in conjunction with the R key. Then, hit Enter after entering devmgmt.msc in the window that appears. In the new box that appears, go to the Update & Security subheading, and from there, choose Windows Defender from the list of available options on the left.
Authenticating an account on GitHub Enterprise
Launch tracer.exe and begin capturing data, then start the Backup Exec services. Error responses occur when SCSI commands do not complete their intended operation due to an error. Like Check Conditions, these errors normally contain additional sense key data that contains information regarding the condition that caused the failure. These errors are marked as an ‘E’ under the ‘Check’ column in tracer. The above command is a Test Unit Ready command, which is a SCSI command that queries the device to see if the device is ready for read and write operations. In this case, there is a SCSI reservation conflict preventing such an operation.
SQL errors can also be logged in a separate file using the SQL_ERROR_LOG plugin. User password management – authentication methods such as password autofill keychain. Apps cannot access this information without user permission. /var/log/auth.log or /var/log/secure – all authentication and authorization logs. RedHat-based systems store these in the auth.log folder while Debian-based systems store them in the secure folder. More than 2,100 enterprises around the world rely on Sumo Logic to build, run, and secure their modern applications and cloud infrastructures.
If you are seeing errors such as this for your job, you’ll want to take steps to understand the scope of the issue so as to best determine where the actual problem is. We offer a set of Troubleshooting Steps in this doc to help you do this. If you see the ‘Not Connected’ error after clicking on the Globus icon, then the GCP software is not able to connect to the Globus service. The Globus Connect Personal software must be able to talk to the Globus service during the install process, as well as during normal endpoint operation. If you encounter a permissions issue when attempting to install the Globus Connect Personal software, then you may see an error something like the above.